Immunity for the AI Threat Era
An AI-powered security layer trained on real adversaries, designed to detect and adapt to evolving threats.



FEATURES
FEATURES
FEATURES
Threat intelligence

Device Fingerprinting
Identify account farms, link malicious behaviour across devices, and fast-track trusted returning users without friction.


Device Fingerprinting
Identify account farms, link malicious behaviour across devices, and fast-track trusted returning users without friction.


Device Fingerprinting
Identify account farms, link malicious behaviour across devices, and fast-track trusted returning users without friction.


True Location Intelligence
Reveal where users actually are, even behind VPNs and proxies, and pinpoint real-world geography with precision.



True Location Intelligence
Reveal where users actually are, even behind VPNs and proxies, and pinpoint real-world geography with precision.



True Location Intelligence
Reveal where users actually are, even behind VPNs and proxies, and pinpoint real-world geography with precision.



Bot Activity Intelligence
Stops automated account creation, onboarding funnels, credential stuffing, and synthetic bot interactions before they cause damage.


Bot Activity Intelligence
Stops automated account creation, onboarding funnels, credential stuffing, and synthetic bot interactions before they cause damage.


Bot Activity Intelligence
Stops automated account creation, onboarding funnels, credential stuffing, and synthetic bot interactions before they cause damage.


Bot Activity Intelligence
Stops automated account creation, onboarding funnels, credential stuffing, and synthetic bot interactions before they cause damage.

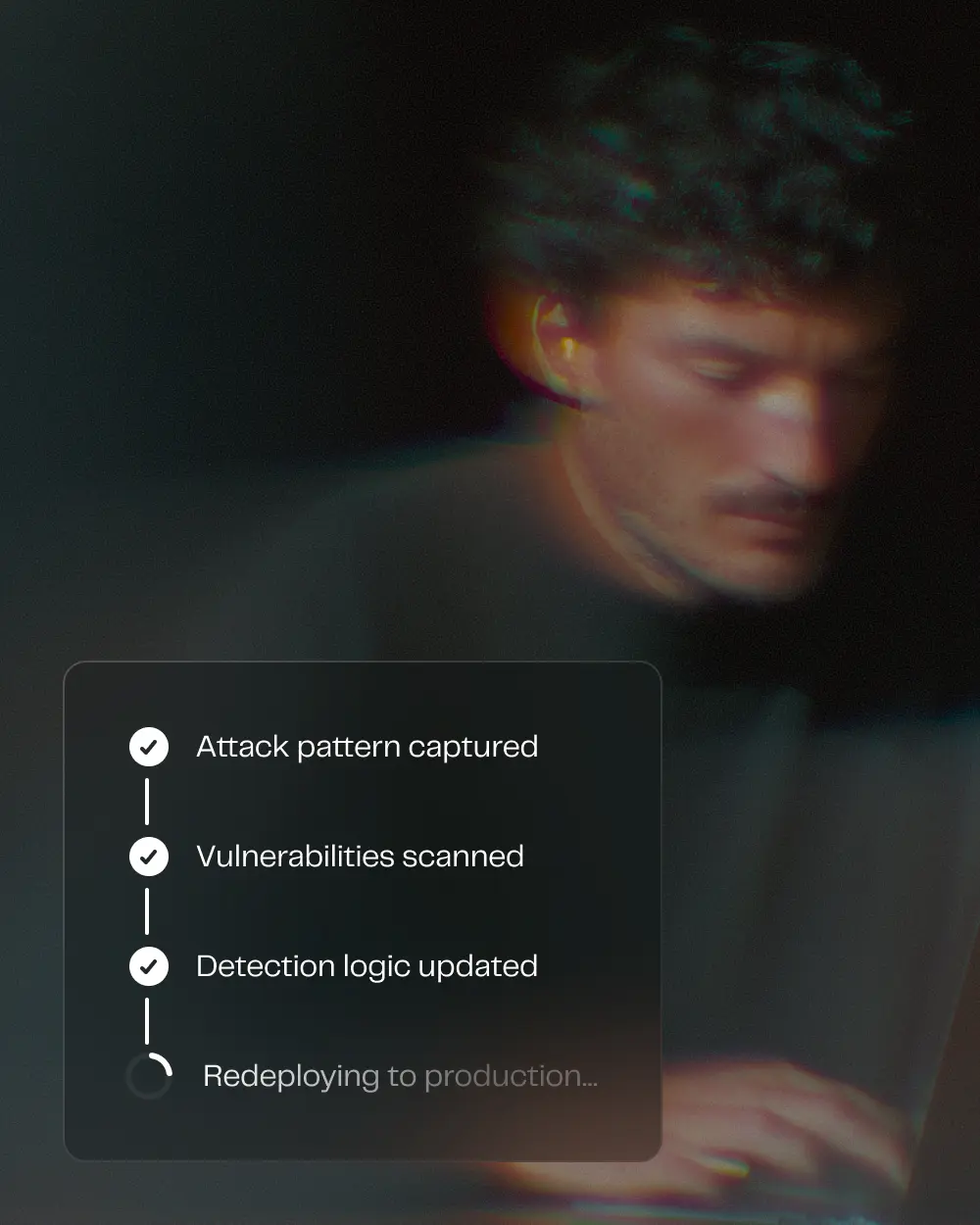


REDTEAM
REDTEAM
REDTEAM
A self-healing system
RedTeam operates as an adversarial R&D system, continuously simulating real-world attack techniques — from VPN evasion to synthetic identities and coordinated device networks.
TECHNOLOGY
TECHNOLOGY
TECHNOLOGY
Security proven at scale
$
0
b+
Assets under protection
$
0
b+
Assets under protection
$
0
b+
Assets under protection
0
m+
Daily active users protected
0
m+
Daily active users protected
0
m+
Daily active users protected
#
0
Benchmarked detection accuracy
#
0
Benchmarked detection accuracy
#
0
Benchmarked detection accuracy
SETUP
SETUP
SETUP
Simple integration
Install in minutes
An easy to install single-line SDK install with no user disruption

Unparalleled clarity
Expose threats and behavior traditional tools can’t see.

Flexible for your stack
flexibly fits cleanly into your existing security and risk infrastructure.


Continuously evolving defense
AI-driven insight from ethical hackers strengthens protection for everyone.
243 live ethical hackers
TEAM
TEAM
TEAM
Who we are

Oliver Quie
CEO
10 years in Identity & Behavioural Analytics

Oliver Quie
CEO
10 years in Identity & Behavioural Analytics

Oliver Quie
CEO
10 years in Identity & Behavioural Analytics

Oscar Hayek
CTO
AI engineering, Fmr-Aus Government

Oscar Hayek
CTO
AI engineering, Fmr-Aus Government

Oscar Hayek
CTO
AI engineering, Fmr-Aus Government

Tom Ryan
CPO
Fmr-Cambridge ML Researcher

Tom Ryan
CPO
Fmr-Cambridge ML Researcher

Tom Ryan
CPO
Fmr-Cambridge ML Researcher

Tony Pepper
Board Member
Co-founder Egress

Tony Pepper
Board Member
Co-founder Egress

Tony Pepper
Board Member
Co-founder Egress

© 2026 Innerworks. All rights reserved.

© 2026 Innerworks. All rights reserved.

© 2026 Innerworks. All rights reserved.